select the best answer. which of the following are breach prevention best practices
A single technology cannot provide complete protection. In a hyper-connected business world organizational leaders understand that data breaches are a fact of life.
Which of the following are breach prevention best practices.

. This quiz covers the content in Cybersecurity Essentials 11 Chapter 7. Tripwire is used to assess if network devices are compliant with network security policies. Access only the minimum amount of PHIpersonally identifiable information PII necessary.
PCs cell phones PDAs and the network says Pappas. It describes a process and its elements for. What is the best.
Top 15 cybersecurity best practices. Choose the best answer adopting a best-in-suite approach to securityadopting a best-in-suite approach to security. Logoff or lock your workstation when it is unattended.
Tip 9 Avoid using public networks. Phishing Prevention Best Practices. True Select the best answer.
AResidents should always be restricted to their rooms BResidents with indwelling medical devices or wounds should be restricted to their rooms CResidents with. Promptly retrieve documents containing PHIPHI from the printer. Final Quiz Form B.
Convene a workgroup to research threats vulnerabilities. Notify individuals and the Commissioner if required. Share this link with a friend.
Before you can prevent a data breach. Access only the minimum amount of PHIpersonally identifiable information PII necessary B. Reduce the level of employee negligence.
SuperScan is a Microsoft port scanning software that detects open TCP and UDP ports on systems. The following are breach prevention best practices. Now with the GDPR in full effect we will likely see these costs increase.
This paper focuses solely on the aspects of re-establishing best practices safety. Attracting new customers or regaining the loyalty of existing customers following a successful and widely publicized breach is very difficult task. These include.
Select the best answer. Which of the following are breach prevention best practices. Please select the best response.
He recommends campuses have firewalls. All of the above When must a breach be reported. Which of the following are breach prevention best practices All of the above.
In the United States the average total cost of a data breach stands at 819 million more than twice the global average. Select the best answer. An individuals first and last name and the medical diagnosis in a physicians progress report correct Individually identifiable health information IIHI in employment records held by a covered entity CE in its role as an employer.
Logoff or lock your workstation when it is unattended. Which of the following is the best practice regarding decisions to restrict residents to their rooms while on Transmission-Based Precautions. All of the above.
There are Microsoft best practices best practices and practices. The following are breach prevention best practices. The best way to avoid being a victim of a breach is to prioritize data security.
Which of the following are common causes of breaches. Those who use SharePoint best practices often follow Microsoft ones too because of their safety and security. The solution Cynet Network Analytics continuously monitors network traffic to trace and prevent malicious activity that is otherwise invisible such as credential theft and data exfiltration.
In addition there is a number of other best practices that users can use regardless of the presence of any specialized software in order to prevent phishing. SIEM is used to provide real-time reporting of security events on the network. Are you following best practices for data security and breach prevention.
The best way to avoid being the victim of a breach is by prioritizing security through various best practices processes and procedures and then detailing these in a policy. Promptly retrieve documents containing PHIPHI from the printer D. Endpoint Protection and EDR.
Assess the data breach by gathering the facts and evaluating the risks including potential harm to affected individuals and where possible taking action to remediate any risk of harm. Promptly retrieve documents containing PHIPHI from the printer. The patterns presented above provide general guidelines for spotting phishing emails.
Identity sensitive data collected stored transmitted or processes. Results of an eye exam taken at the DMV as part of a driving test. Choose the best answerWhich action is most likely to simplify security staff training improve integration between security components and reduce risk to the business.
Promptly retrieve documents containing PHIPHI from the printer D. Logoff or lock your workstation when it is unattended C. Which of the following are categories for punishing violations of federal health care laws.
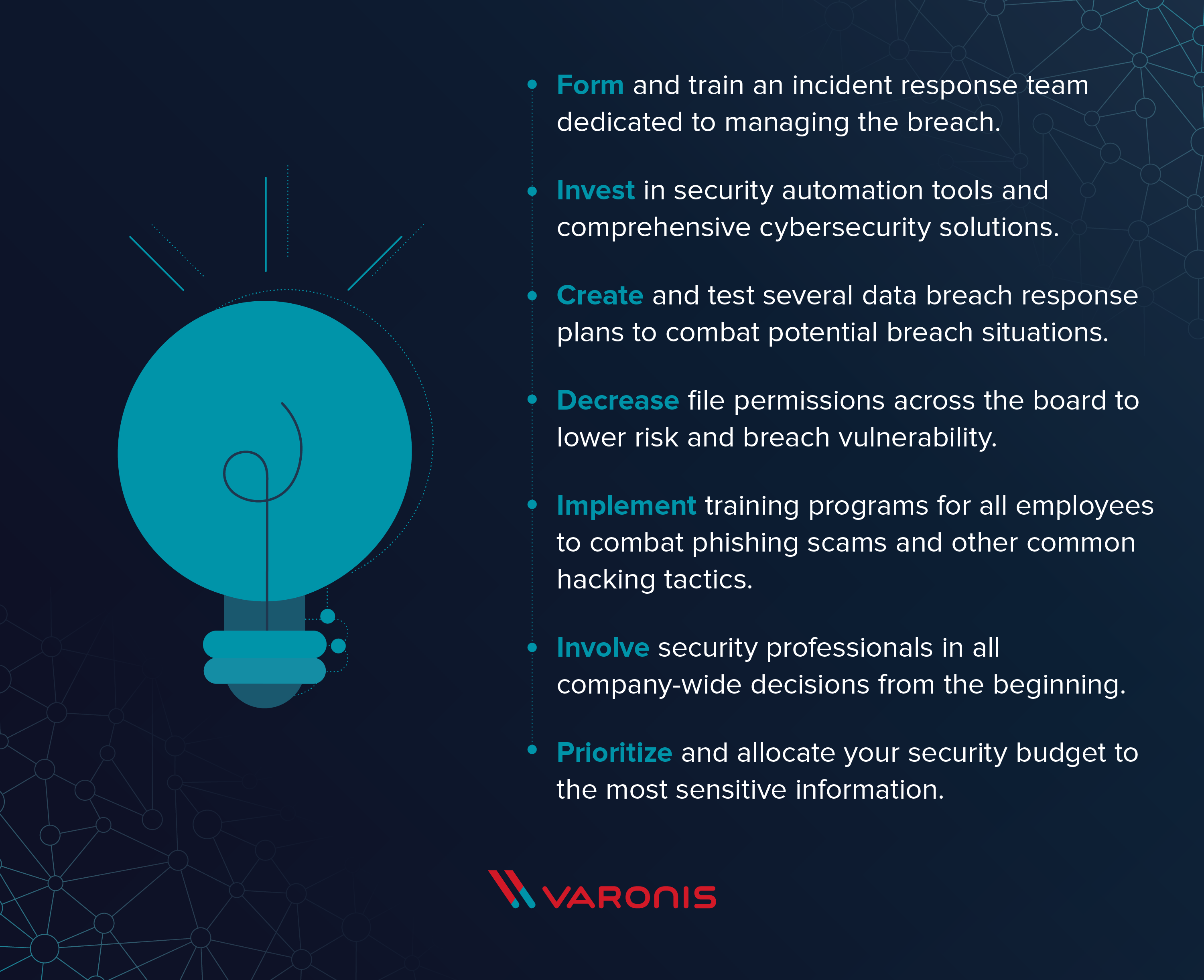
However these 30 best practices for preventing a data breach can reduce the risk and respond to an attack more effectively. Heres our IT security best practices checklist that you can rely on to find answers to these questions and prevent cyber attacks. It is designed to provide an additional opportunity to practice the skills and knowledge presented in the chapter and to help prepare for the final quiz.
Start by brainstorming what you want to include in your data security policy or use a data security policy template to skip this step. Access only the minimum amount of PHIpersonally identifiable information PII necessary. Contain the data breach to prevent any further compromise of personal information.
Nmap and Zenmap are low-level network scanners available to the public. IIHI of persons deceased more than 50. They need to be secure at the host eg.
A user is proposing the purchase of a patch management solution for a company. Employ a people-centric security approach.

7 Key Steps To Investigate A Data Breach With Checklist Ekran System

7 Best Practices For Third Party Security Risk Management Ekran System
Data Breach Response Times Trends And Tips

Data Loss Prevention Best Practices Endpoint Protector
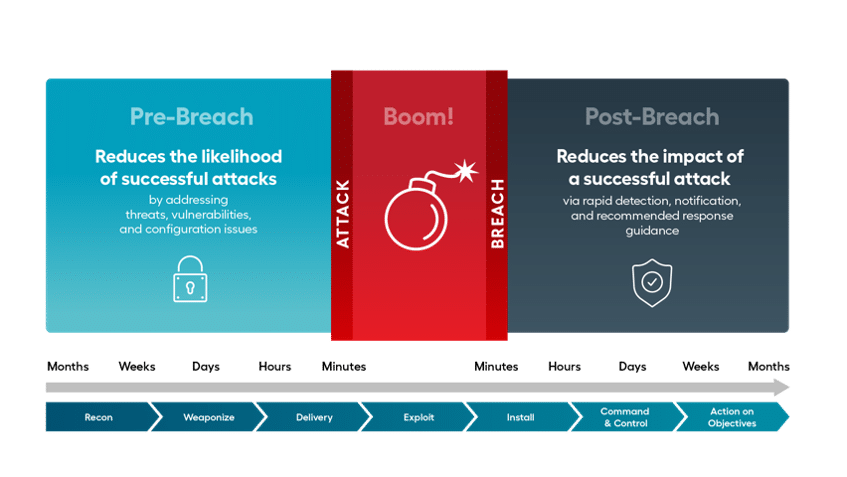
Managed Detection And Response Mdr Solutions Services Alert Logic

10 Secure File Sharing Options Tips And Solutions
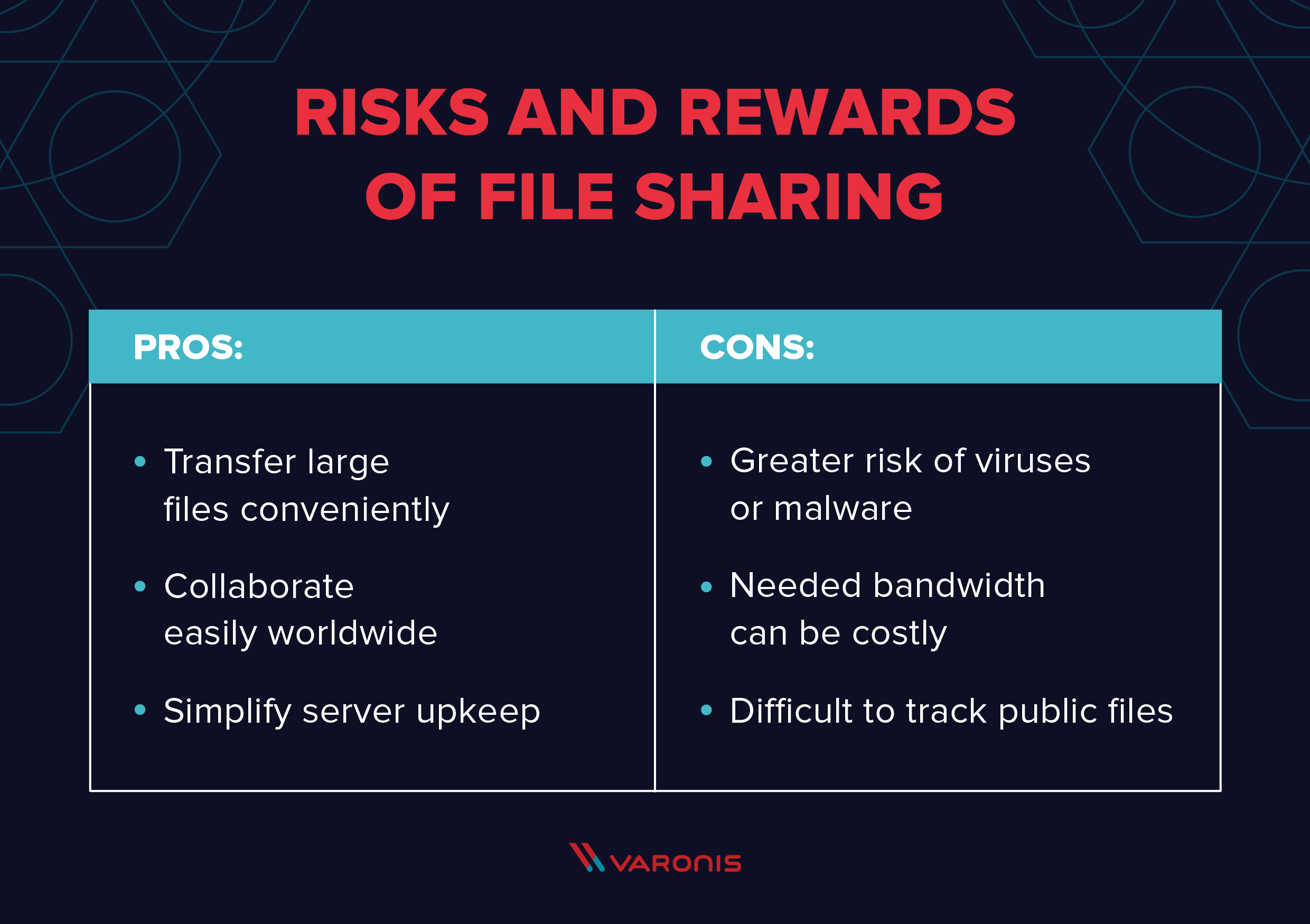
10 Secure File Sharing Options Tips And Solutions

Kubernetes Best Practices 8 Tips To Improve Security Cycode

7 Best Practices For Third Party Security Risk Management Ekran System

Unauthorized Access 5 Best Practices To Avoid Data Breaches
Frequently Asked Questions About Data Loss Prevention Endpoint Protector

10 Business Ethics Online Courses Edapp Microlearning Programs

Data Loss Prevention What Is Dlp How Does It Work

7 Key Steps To Investigate A Data Breach With Checklist Ekran System

8 Infrastructure As Code Best Practices For Security Cycode
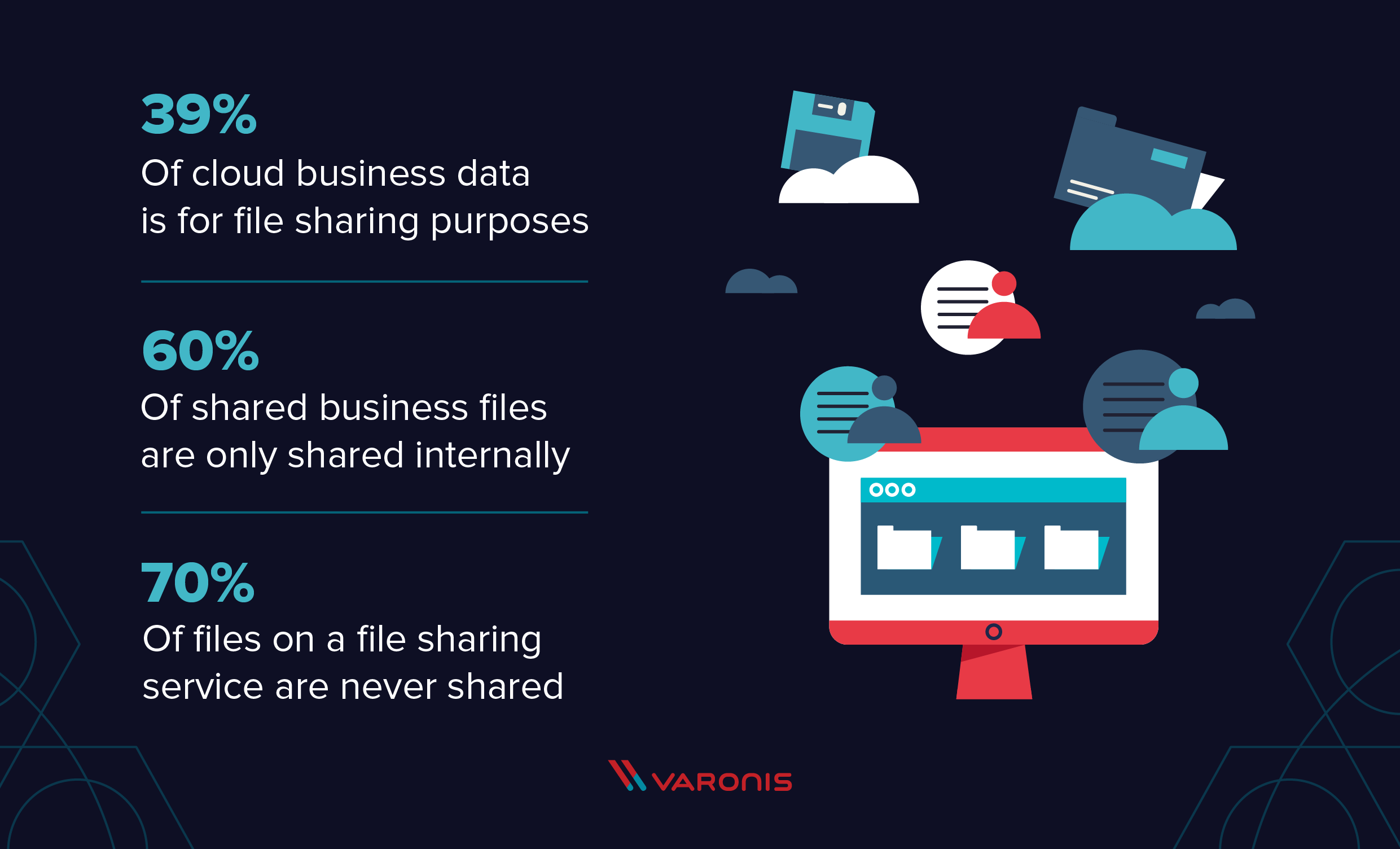
10 Secure File Sharing Options Tips And Solutions